Turns out it is pretty easy, as you should see below. And you do not even need to install a paid iPhone sniffer app, you can just use wireshark on your computer and sniff iPhone traffic. First, check your UDID/AdID/AIFA. Connect your iPhone to the mac through a USB cable; Install and open Xcode; In the Xcode menu bar, go to Window. Download the Metasploit source code for installation using the link provided below and do not download the.run file from the Metasploit download page. Download the Metasploit tar file from: Once the download is complete, untar the file. So, my question is, how can I make tcpdump in Centos display mac address like my macOS?, ie, display both 'in' and 'out' mac address. How to install Java 8 on Mac. Extract useful data from wireshark/tcpdump. Tcpdump - How to check if server received packet (acknowledged) 0. Sudo tcpdump -i en1 -s 128 port 53 -i Sets which interface to listen to. En1 for me is the AirPort wifi card. En0 would be the ethernet card.s sets the number of bytes to “sniff” or “snarf” per call that goes through this interface. 128 gives us a bit better coverage than the default 68 bytes. Tcpdump for windows free download - Microsoft Office 2011, Adobe Photoshop CC, uTorrent, and many more programs. Enter to Search. My Profile Logout. Install Windows using Intel devices.
- Install Tcpdump Linux
- Install Tcpdump On Windows
- How To Use Tcpdump
- How To Install Tcpdump Windows
- How To Install Tcpdump For Macbook Pro
- How To Install Tcpdump On Mac
From charlesreid1
Install Tcpdump Linux
- 1Installing
- 2Basic Usage
- 2.2Controlling Output
- 4More Flags
- 5Analysis
Linux
tcpdump should come with your distro, but if it doesn't, use aptitude or your package manager to install:
Once you've done that, you can list your network devices:
Pick out which ones you want to listen to.
Mac
tcpdump comes with Mac. Man page for tcpdump: https://developer.apple.com/library/mac/documentation/Darwin/Reference/ManPages/man1/tcpdump.1.html
List your network devices:
Pick out which ones you want to listen to.
You may need to run tcpdump as sudo to access certain information from the hardware.
Tcpdump options can vary from platform to platform (e.g. mac vs linux) but this guide will cover some universal usage.
The simplest way to use tcpdump is to do an unfiltered packet capture - no filters on packets, so everything is captured.
The bare minimum you'll have to specify is a network interface. You may want to specify a file, too.
The -i and -w flags
To specify a network device you want to listen to, use the -i flag (for interface). Also specify an output file with the -w flag:
-w prevents your computer from having a meltdown trying to print every single packet in a busy place.
You can monitor multiple interfaces by specifying a list: -i en0,en1
If you are using wireless, you'll need to use additional commands to control the channel your wireless card is listening to.
Controlling Output
To control output, you can have tcpdump create a new pcap file every N seconds, or every N megabytes.
G flag
Use the G flag to create a new pcap file every N seconds:
If you use the G flag without the C flag (see below), you specify new filenames with strftime date/time format when you pass the filename to the -w flag.
This command makes a new pcap file every 100 seconds:
C flag
The C flag sets the maximum pcap file size, in millions of bytes. New files will have a common name with an incrementing number at the end. From the man page:
W flag
The W flag will limit the number of output files, so that tcpdump will begin to overwrite the first file once it has finished writing to the Nth file:
Install Tcpdump On Windows
More instructions on capturing wireless packets with Tcpdump: Tcpdump/Wireless
Faster Packet Capture
To minimize overhead processing packets and maximize the number of packets captured, you can turn off host name resolution with the -n flag. This also makes things slightly more readable.
Writing Packets To File
If you want to force tcpdump to write every packet to the output file as it is received, rather than waiting until its input buffer is full, you can use the U flag. Note that this will be slower and should only be done when traffic is light - otherwise excessive disk writes will bog things down.
From the man page:
You can also use tcpdump to analyze a pcap file.
Reading Packets
To read packet data, run tcpdump with the -r flag (for read):
Counting Packets
How To Use Tcpdump
Not sure if this will work:
This will give you a count of the total number of packets in the pcap file.
Parsing Information
You can parse information by column using the cut utility.

The output has the fields:

How To Install Tcpdump Windows
Today, we are working about capturing the PACP LOGS with the help of Wireshark. Organization following logs are helpful to investigate issues identified with network availability. Tcpdump utility can be utilized to gather logs from KALI Linux.
Wireshark is using for network tracing logs in Windows/Linux/macOS.
So let’s start…
Requirements:
- Windows OS
- Wireshark
FIRST Step to Download the free Wireshark utility and install
Download the free Wireshark utility for Windows. If you do not want to install Wireshark on your system, then it is recommended to download and run the portable version.
Step 2 Run Wireshark and Note the IP of the source and target device
Select Capture – > Options

Select comparing network connector you are utilizing for your organization association and select the Start button
In the event that you need to screen association through a specific port number, you can set it up as well. In Capture Filter type the port you need to screen, for example tcp port 443 or tcp port 44445
In case you know that backup will not fail immediately, it means WireShark should be executed during some extended time (20 minutes +) it is a good idea to write the information to a file right after start. You can choose a file in the Output tab and set traffic and time limits for logs collection:
Step 3 Reproduce the issue without shutting the Wireshark application
Step 4 Click Capture – > Stop after the issue is imitated:
Step 5 Spare the caught information in default design (pcap) by clicking File – > Save as

Result
Hope you will get to know to capture PCAP logs in Wireshark.
Also Read: Wireshark Commands Cheatsheet
How To Install Tcpdump For Macbook Pro
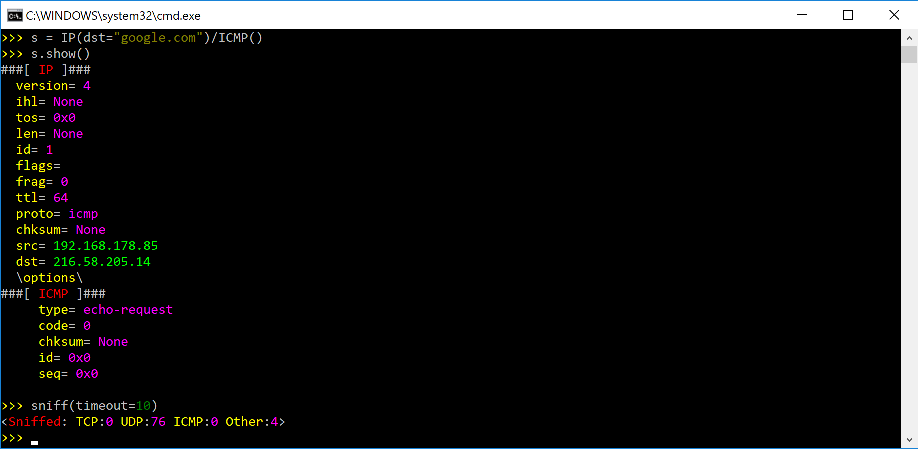
How To Install Tcpdump On Mac
